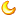Default in switchfin firmware
allowauthreject = yes- Global Settings:
- ----------------
- SIP Port: 5060
- Bindaddress: 0.0.0.0
- Videosupport: No
- AutoCreatePeer: No
- Allow unknown access: No
- Allow subscriptions: Yes
- Allow overlap dialing: Yes
- Promsic. redir: No
- SIP domain support: No
- Call to non-local dom.: Yes
- URI user is phone no: No
- Our auth realm Realm
- Realm. auth: No
- Always auth rejects: Yes
- Call limit peers only: No
- Direct RTP setup: No
- User Agent: SwitchFin PBX
- MWI checking interval: 10 secs
- Reg. context: (not set)
- Caller ID: asterisk
- From: Domain:
- Record SIP history: Off
- Call Events: Off
- IP ToS SIP: none
- IP ToS RTP audio: EF
- IP ToS RTP video: CS3
- T38 fax pt UDPTL: No
- RFC2833 Compensation: No
- SIP realtime: Disabled
- Global Signalling Settings:
- ---------------------------
- Codecs: 0x10e (gsm|ulaw|alaw|g729)
- Codec Order: alaw:20,ulaw:20,gsm:20,g729:20
- T1 minimum: 100
- No premature media: No
- Relax DTMF: No
- Compact SIP headers: No
- RTP Keepalive: 0 (Disabled)
- RTP Timeout: 0 (Disabled)
- RTP Hold Timeout: 0 (Disabled)
- MWI NOTIFY mime type: application/simple-message-summary
- DNS SRV lookup: Yes
- Pedantic SIP support: No
- Reg. min duration 60 secs
- Reg. max duration: 3600 secs
- Reg. default duration: 120 secs
- Outbound reg. timeout: 20 secs
- Outbound reg. attempts: 0
- Notify ringing state: Yes
- Notify hold state: No
- SIP Transfer mode: open
- Max Call Bitrate: 384 kbps
- Auto-Framing: No
- Default Settings:
- -----------------
- Context: default
- Nat: Always
- DTMF: rfc2833
- Qualify: 2000
- Use ClientCode: No
- Progress inband: Never
- Language: (Defaults to English)
- MOH Interpret: default
- MOH Suggest:
- Voice Mail Extension: asterisk
|